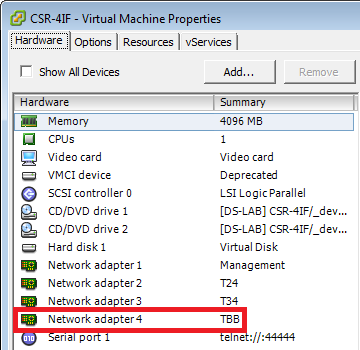
Background: Python-Requests wants to verify https-certificates, which makes sense to me.
– but my VCenter uses a self-signed Certificate
$ python
Python 2.7.15rc1 (default, Apr 15 2018, 21:51:34)
[GCC 7.3.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> import requests
>>> requests.get("https://<vcenter-ip>")
Traceback (most recent call last):
File "<stdin>", line 1, in <module>
File "/usr/lib/python2.7/dist-packages/requests/api.py", line 72, in get
return request('get', url, params=params, **kwargs)
File "/usr/lib/python2.7/dist-packages/requests/api.py", line 58, in request
return session.request(method=method, url=url, **kwargs)
File "/usr/lib/python2.7/dist-packages/requests/sessions.py", line 520, in request
resp = self.send(prep, **send_kwargs)
File "/usr/lib/python2.7/dist-packages/requests/sessions.py", line 630, in send
r = adapter.send(request, **kwargs)
File "/usr/lib/python2.7/dist-packages/requests/adapters.py", line 506, in send
raise SSLError(e, request=request)
requests.exceptions.SSLError: HTTPSConnectionPool(host='192.168.2.13', port=443): Max retries exceeded with url: / (Caused by SSLError(SSLError(1, u'[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed (_ssl.c:726)'),))
Don’t think about ignoring certificate errors 😉
Prerequisites
sudo apt-get install unzip
Download the certificate from the VCenter:
wget --no-check-certificate https://<vcenter-ip>/certs/download mv download download.zip unzip download.zip
Install the certificate:
cd certs $ ls -l total 8 -rw-r--r-- 1 administrator administrator 1294 Apr 29 2016 d2f59c0d.0 -rw-r--r-- 1 administrator administrator 702 Oct 15 14:36 d2f59c0d.r0 $ export REQUESTS_CA_BUNDLE=d2f59c0d.0
Now Python.requests validates the vCenter:
$ python
Python 2.7.15rc1 (default, Apr 15 2018, 21:51:34)
[GCC 7.3.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> import requests
>>> requests.get("https://<vcenter-ip>")
<Response [200]>
Add the Export to ~/.bashrc
sudo vi ~/.bashrc
at the end of the file
export REQUESTS_CA_BUNDLE=~/certs/d2f59c0d.0




![Hardware virtualization: [x] Expose hardware assisted virtualization to guest-OS](https://allones.de/wp-content/uploads/2018/02/kvm-1-hardwarevirtualisierung.png)