Sometimes I need a lightweight straight-forward toolset to provision, modify or delete vSphere-Objects.
Installation was a nightmare in former times, but vSphere CLI Release 6.5 works with Ubuntu server 16.04.3 LTS „out of the box“.
And – it’s compatible with ESXi 6.0 hosts. (don’t waste time trying to install vSphere CLI Release 6.0 on a current Linux Server)
Consider the docs:
vSphere CLI Documentation
VMware [Code] vSphere-CLI 6.5
Download the 64-bit Archive
Use the vmware-search or Google…
„Download VMware vSphere Command Line Interface 6.5“ might be a promising query.
I downloaded VMware-vSphere-CLI-6.5.0-4566394.x86_64.tar.gz using my Windows Machine.
Transfer the Archive to the Linux-VM using SCP
Since SCP is available at the Linux-VM and this protocol is fast and secure i don’t see the requirement to think about alternative protocols.
- I’d suggest to use „PSCP“ from the PuTTY-Suite.
c:\temp>pscp -2 VMware-vSphere-CLI-6.5.0-4566394.x86_64.tar.gz USER_NAME@LINUX_VM_IP:VMware-vSphere-CLI-6.5.0-4566394.x86_64.tar.gz
USER_NAME@LINUX-VM-IP's password: USER_PASS
VMware-vSphere-CLI-6.5.0- | 52264 kB | 3266.5 kB/s | ETA: 00:00:00 | 100%
Disable unneded SSH-Localization
The VMware-Installer seems to not expect non-US-Computers, so avoid automatic special characters from Germany in the SSH-shell.
user@snmp-server:~$ sudo cp /etc/ssh/ssh_config /etc/ssh/ssh_config.bak
Just comment the „SendEnv LANG LC_*“-line:
user@snmp-server:~$ sudo joe /etc/ssh/ssh_config
like this:
user@snmp-server:~$ diff /etc/ssh/ssh_config.bak /etc/ssh/ssh_config
53c53
< SendEnv LANG LC_*
---
> # SendEnv LANG LC_*
Install Prerequisites
Taken from Installing Prerequisite Software for Linux Systems with Internet Access „Ubuntu 16.04 64-bit“-Section:
sudo apt-get install lib32z1 lib32ncurses5 build-essential uuid uuid-dev libssl-dev perl-doc libxml-libxml-perl libcrypt-ssleay-perl libsoap-lite-perl libmodule-build-perl
Install vSphere CLI
user@snmp-server:~$ tar xzf VMware-vSphere-CLI-6.5.0-4566394.x86_64.tar.gz
user@snmp-server:~$ sudo vmware-vsphere-cli-distrib/vmware-install.pl
Creating a new vSphere CLI installer database using the tar4 format.
Installing vSphere CLI 6.5.0 build-4566394 for Linux.
You must read and accept the vSphere CLI End User License Agreement to
continue.
Press enter to display it.
VMware® vSphere Software Development Kit License Agreement
…
Do you accept? (yes/no) yes
Thank you.
WARNING: The http_proxy environment variable is not set. If your system is
using a proxy for Internet access, you must set the http_proxy environment
variable .
If your system has direct Internet access, you can ignore this warning .
WARNING: The ftp_proxy environment variable is not set. If your system is
using a proxy for Internet access, you must set the ftp_proxy environment
variable .
If your system has direct Internet access, you can ignore this warning .
Please wait while configuring CPAN ...
Below mentioned modules with their version needed to be installed,
these modules are available in your system but vCLI need specific
version to run properly
Module: ExtUtils::MakeMaker, Version: 6.96
Module: Module::Build, Version: 0.4205
Module: Net::FTP, Version: 2.77
Module: LWP::Protocol::https, Version: 6.04
Do you want to continue? (yes/no) yes
Be patient, do something else in the meantime…
Please wait while configuring perl modules using CPAN ...
CPAN is downloading and installing pre-requisite Perl module "Devel::StackTrace" .
CPAN is downloading and installing pre-requisite Perl module "Class::Data::Inheritable" .
CPAN is downloading and installing pre-requisite Perl module "Convert::ASN1" .
CPAN is downloading and installing pre-requisite Perl module "Crypt::OpenSSL::RSA" .
CPAN is downloading and installing pre-requisite Perl module "Crypt::X509" .
CPAN is downloading and installing pre-requisite Perl module "Exception::Class" .
CPAN is downloading and installing pre-requisite Perl module "UUID::Random" .
CPAN is downloading and installing pre-requisite Perl module "Archive::Zip" .
CPAN is downloading and installing pre-requisite Perl module "Path::Class" .
CPAN is downloading and installing pre-requisite Perl module "Class::MethodMaker" .
CPAN is downloading and installing pre-requisite Perl module "UUID" .
CPAN is downloading and installing pre-requisite Perl module "Data::Dump" .
CPAN is downloading and installing pre-requisite Perl module "Socket6 " .
CPAN is downloading and installing pre-requisite Perl module "IO::Socket::INET6" .
CPAN is downloading and installing pre-requisite Perl module "Net::INET6Glue" .
In which directory do you want to install the executable files? [/usr/bin]
Please wait while copying vSphere CLI files...
The installation of vSphere CLI 6.5.0 build-4566394 for Linux completed
successfully. You can decide to remove this software from your system at any
time by invoking the following command:
"/usr/bin/vmware-uninstall-vSphere-CLI.pl".
This installer has successfully installed both vSphere CLI and the vSphere SDK for Perl.
Enjoy,
--the VMware team
Give it a try: Add a vSwitch with 5 Portgroups
user@snmp-server:~$ vicfg-vswitch --help
Synopsis: /usr/bin/vicfg-vswitch OPTIONS [<vswitch>]
Command-specific options:
--add
-a
Add a new virtual switch
--add-dvp-uplink
-P
Add an uplink adapter (pnic) to a DVPort (valid for vSphere 4.0 and later)
--add-pg
-A
Add a portgroup to a virtual switch
...
Define credentials to login into the vSphere-Environment
user@snmp-server:~$ export VI_SERVER=%SERVER_IP_OR_HOSTNAME%
user@snmp-server:~$ export VI_USERNAME=%VSPHERE_USER_NAME%
user@snmp-server:~$ export VI_PASSWORD=%VSPHERE_USER_PASS%
Create the Switch and the portgroups
user@snmp-server:~$ vicfg-vswitch --add "RTR_LAB" -h %ESXi-HOST-IP%
user@snmp-server:~$ vicfg-vswitch -A "T12" "RTR_LAB" -h %ESXi-HOST-IP%
user@snmp-server:~$ vicfg-vswitch -A "T13" "RTR_LAB" -h %ESXi-HOST-IP%
user@snmp-server:~$ vicfg-vswitch -A "T24" "RTR_LAB" -h %ESXi-HOST-IP%
user@snmp-server:~$ vicfg-vswitch -A "T34" "RTR_LAB" -h %ESXi-HOST-IP%
user@snmp-server:~$ vicfg-vswitch -A "T45" "RTR_LAB" -h %ESXi-HOST-IP%
Isn’t it beautiful? 😉
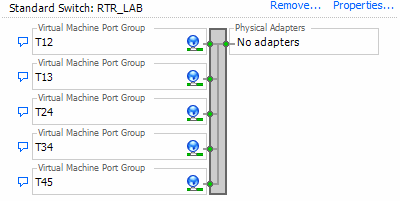
And i think, even with downloading and installing vSphere-CLI it was faster than GUI-clicking to create this vSwitch 😉
