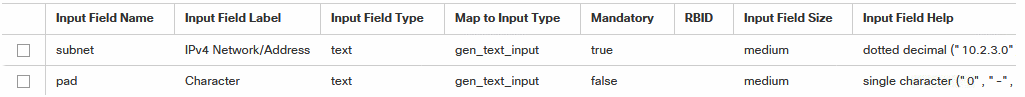
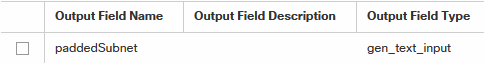
Since I still want to build a centralized solution for automated configuration of RMON-alarms to monitor Cisco cbQoS-packet/drop-counters a solution to retrieve and modify device configurations was needed.
The NAPALM (Network Automation and Programmability Abstraction Layer with Multivendor support) Framework seems to provide the required features.
NAPALM Installation
Some NAPALM-IOS dependencies have to be fulfilled first.
sudo apt-get install -y --force-yes libssl-dev libffi-dev python-dev python-cffi
The „partial installation“ seems to be not working anymore, the full installation uses some KB more ressources, not worth to think about the partial installation…
pip install napalm
IOS Preperation
To allow remote-access to the centralized NAPALM server these features need to be enabled in each IOS device:
- Remote-Access via SSH,
- SCP (Secure Copy),
- the IOS „Archive“-feature is the foundation of NAPALM config-operations.
IOS-RTR#conf t Enter configuration commands, one per line. End with CNTL/Z. ! AAA preferred for production-systems, of course IOS-RTR(config)#username rmond privilege 15 secret rmondpass ! required IOS-RTR(config)#ip scp server enable ! no annoying [yes/no]-prompts for file-operations anymore IOS-RTR(config)#file prompt quiet ! create the folder in the filesystem for the Archive IOS-RTR(config)#do mkdir bootflash:/ARCHIVE IOS-RTR(config)#archive IOS-RTR(config-archive)#path bootflash:/ARCHIVE/bak-
Explore Napalm
Go the the python shell:
user@snmp-server:~$ python
>>> import napalm
>>> iosdriver = napalm.get_network_driver('ios')
Autodiscovery of the router-filesystem doesn’t work, i know the filesystem of my router and pass it as „optional argument“ to router-object.
*** todo: troubleshoot/fix the autodiscovery ***
>>> router = iosdriver(hostname='192.168.2.72', username='rmond', password='rmondpass',
optional_args={'port': 22, 'dest_file_system': 'bootflash:'})
>>> router.open()
Go to the router cli-shell:
- user „rmond“ is logged in
IOS-RTR#who
Line User Host(s) Idle Location
* 1 vty 0 user idle 00:00:00 192.168.2.109
2 vty 1 rmond idle 00:00:02 192.168.2.89
Back to python, try some NAPALM-functions.
>>> print router.get_facts()
{u'os_version': u'CSR1000V Software (X86_64_LINUX_IOSD-UNIVERSALK9-M), Version 15.4(2)S3, RELEASE SOFTWARE (fc2)',
u'uptime': 657600, u'interface_list': [u'GigabitEthernet1', u'GigabitEthernet2', u'GigabitEthernet3'], u'vendor': u'Cisco',
u'serial_number': u'afdökjl0123', u'model': u'CSR1000V', u'hostname': u'IOS-RTR', u'fqdn': u'IOS-RTR.lab.local'}
Execute interactive EXEC-Commands.
>>> cliping=['ping 192.168.2.1']
>>> print router.cli(cliping)
{'ping 192.168.2.1': u'Type escape sequence to abort.\n
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:\n!!!!!\n
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms'}
Fetch the current running-config.
>>> clishowrun=['show running-config']
>>> print router.cli(clishowrun)
{'show running-config': u'Building configuration...\n\nCurrent configuration : 2411 bytes\n!\n
! Last configuration change at 12:52:32 UTC Fri Nov 24 2017 by user\n! NVRAM config last updated at 10:24:26 UTC Fri Nov 24 2017 by user\n!\n
version 15.4\nservice timestamps debug datetime msec\nservice timestamps log datetime msec\n
...rmon event 10 log owner RMONevent\nrmon event 11 log owner RMONevent\n
rmon alarm 10001 cbQosCMStatsEntry.2.18.65536 300 delta rising-threshold 1 11 falling-threshold 0 10 owner RMONevent\n
...
end'}
Read some lines from the running-config, filter using the pipe.
>>> cligetrmon=['show rmon alarms | inc RMONevent']
>>> print router.cli(cligetrmon)
{'show rmon alarms | inc RMONevent': u'Alarm 10001 is active, owned by RMONevent'}
Log-out if you are finished:
>>> router.close()