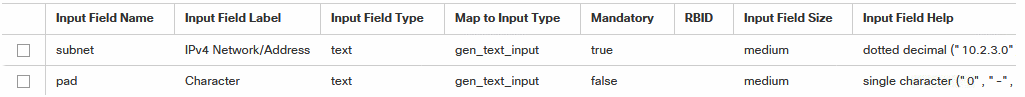
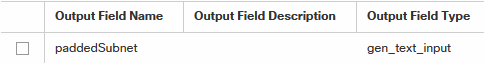
I often need for quick tests a clean Linux Server, a VM nowadays.
I decided to save DRAM in my virtualization host and to:
- not use a GUI
- SSH with standard text-editor are quite fine for me.
Ubuntu 16.04 seems to be a good choice to start with.
- Apply Updates,
sudo apt-get update && sudo apt-get upgrade -y
- install a text-editor //I like joe since it remembers me of turbo-pascal/wordstar 😉
sudo apt-get install joe
- change the hostname of the server-vm
sudo joe /etc/hostnamesudo joe /etc/hosts- add a reliable (static) IP-Address
sudo joe /etc/network/interfaces# The loopback network interface auto lo iface lo inet loopback # The primary network interface auto ens160 iface ens160 inet static address 192.168.2.89 netmask 255.255.255.0 gateway 192.168.2.1 dns-nameservers 192.168.2.1 dns-search lab.local
- reboot the VM
There are other possibilities, but just ifdown/ifup won’t stop the dhcpd-client – the easiest way [but uncoolest, who cares?] is to reboot the VM, takes half a second…
sudo reboot
Todo: Create an UCSD-Workflow for this
Todo: Fix the buggy „always 1“ section-numbering