- 2/3/4-Node Cluster
- no Fabric-Interconnects (FIs)
- Edge-Servers connected to LAN-Switches
- „back-to-Back“-Option for 2-Node Cluster
- only „RF2“-redundancy
networking, computing, virtualization, automation
„Cisco HyperFlex Premier“-Cisco Data Center Enterprise Agreement Tier
VM collects information for 30 days
leverages Information from vCenter
After provisioning a new Cisco CSR1000V-Router this script
and returns this Management IP-Address.
First, install „netaddr“-package.
C:\RH>pip install netaddr
Collecting netaddr
Downloading https://files.pythonhosted.org/packages/ba/97/ce14451a9fd7bdb5a397abf99b24a1a6bb7a1a440b019bebd2e9a0dbec74/netaddr-0.7.19-py2.py3-none-any.whl (1.6MB)
100% |████████████████████████████████| 1.6MB 4.0MB/s
Installing collected packages: netaddr
Successfully installed netaddr-0.7.19
Obviously far to much hard-coded stuff, just as an example 😉 waiting for a CDP-Neighbor to appear with the following properties:
at the interface
#! /usr/bin/env python
from scapy.all import *
load_contrib("cdp")
from netaddr import IPNetwork, IPAddress
# run it for max. 99 Packets
ip = "0.0.0.0"
wait_for_hostname = "CSR-A"
wait_for_host_in_network = "192.168.56.0/24"
interface="VirtualBox Host-Only Ethernet Adapter"
capturefilter="ether dst 01:00:0c:cc:cc:cc"
while not(IPAddress(ip) in IPNetwork(wait_for_host_in_network)):
p=sniff(iface=interface, count=1, filter=capturefilter)
pkt=p[0]
#print("Packet received",pkt.show())
#is this a CDP-Packet containing a hostname?
if (CDPMsgDeviceID in pkt):
#is this the CDP-Neighbor we're looking for?
device=pkt["CDPMsgDeviceID"].val.decode()
hostname=device.split(".")[0]
#print("Hostname:",hostname)
if (hostname == wait_for_hostname):
#is this a CDP-Packet containing a management-IP-Address?
if (CDPAddrRecordIPv4 in pkt):
ip=pkt["CDPAddrRecordIPv4"].addr
#print("IP-Address found:",ip)
#return the IP-Address to the calling application or the CLI
print(ip)
C:\RH>CSR1000v-Virtual-Box.cmd Enter CSR1000v Hostname:CSR-A Virtual machine 'CSR-A' is created and registered. UUID: 8a9c969e-3895-4a7c-9cbc-5f5551bf1b7b Settings file: 'c:\RH\LAB\VM\CSR-A\CSR-A.vbox' Creating ISO image at c:\RH\LAB\VM\CSR-A\config.iso, 1 Files, Size: 8,00 KB 100% 0%...10%...20%...30%...40%...50%...60%...70%...80%...90%...100% Medium created. UUID: 55ea8df5-7e3c-4485-8e08-9302cb61a09d Waiting for VM "CSR-A" to power on... VM "CSR-A" has been successfully started.
In a second CMD-Box, and… Be patient, of course.
C:\RH>python wait-for-cdpneighbor.py 192.168.56.101
C:\RH>for /f %I in ('python wait-for-cdpneighbor.py 2^> nul') do @(set ROUTER-IP=%I)
The Public-Key for user „labuser“ is part of my baseline-config used to provision the virtual-router.
C:\RH>putty -ssh -i C:\RH\work\putty-rsa-key\labuser.ppk labuser@%ROUTER-IP%
Works, this is a nice preparation for an automated virtual ansible-lab, too!
It’s hard to believe, how easy it is to capture (and to craft) LAN-Data using Python Scapy.
I need to capture CDP-Packets and to extract information like the hostname of the sender and it’s IP-Address.
As an modification of the „ARP-Monitor“-example taken from the manual Using scapy in your tools.
nothing special: pip install
C:\RH>pip install scapy
Collecting scapy
Downloading https://files.pythonhosted.org/packages/68/01/b9943984447e7ea6f8948e90c1729b78161c2bb3eef908430638ec3f7296/scapy-2.4.0.tar.gz (3.1MB)
100% |████████████████████████████████| 3.1MB 420kB/s
In the tar file C:\Users\RONALD~1.HEI\AppData\Local\Temp\pip-unpack-4jm9kde1\scapy-2.4.0.tar.gz the member scapy-2.4.0/README is invalid: unable to resolve link inside archive
Installing collected packages: scapy
Running setup.py install for scapy ... done
Successfully installed scapy-2.4.0
C:\RH>python Python 3.7.0 (v3.7.0:1bf9cc5093, Jun 27 2018, 04:59:51) [MSC v.1914 64 bit (AMD64)] on win32 Type "help", "copyright", "credits" or "license" for more information. >>> from scapy.all import *
>>> ifaces
INDEX IFACE IP MAC
20 VirtualBox Host-Only Ethernet Adapter 192.168.56.1 0A:00:27:00:00:14
22 Intel(R) Dual Band Wireless-AC 8265 172.20.10.2 IntelCor:BD:10:37
4 Intel(R) Ethernet Connection (4) I219-LM 47.11.17.10 BayNetwo:00:DE:11
>>> for i in ifaces.data.keys():
... iface = ifaces.data[i]
... name = str(iface.name)
... wname = iface.data['netid']
... mac = str(iface.mac)
... ip = str(iface.ip)
... print("DESCR:{0}, NAME:{1}, MAC:{2}, IP:{3}".format(wname,name,mac,ip))
...
DESCR:Wi-Fi, NAME:Intel(R) Dual Band Wireless-AC 8265, MAC:74:70:FD:BD:10:37, IP:172.20.10.2
DESCR:VirtualBox Host-Only Network, NAME:VirtualBox Host-Only Ethernet Adapter, MAC:0A:00:27:00:00:14, IP:192.168.56.1
DESCR:ETH_DELL, NAME:Intel(R) Ethernet Connection (4) I219-LM, MAC:00:00:81:00:DE:11, IP:47.11.17.10
The "NAME" is needed as interface-handle >>> interface="VirtualBox Host-Only Ethernet Adapter" >>> p=sniff(iface=interface, count=10) >>> p.display() 0000 Ether / IP / UDP 192.168.56.1:17500 > 255.255.255.255:17500 / Raw 0001 Ether / IP / UDP 192.168.56.1:17500 > 255.255.255.255:17500 / Raw 0002 Ether / IP / UDP 192.168.56.1:17500 > 192.168.56.255:17500 / Raw 0003 Ether / IP / UDP 192.168.56.1:17500 > 255.255.255.255:17500 / Raw 0004 Ether / IP / UDP 192.168.56.1:17500 > 255.255.255.255:17500 / Raw 0005 Ether / IP / UDP 192.168.56.100:bootps > 255.255.255.255:bootpc / BOOTP / DHCP 0006 Ether / IP / UDP 192.168.56.102:50472 > 255.255.255.255:10067 / Raw 0007 Ether / IP / UDP 192.168.56.103:49580 > 255.255.255.255:10067 / Raw 0008 Ether / IP / UDP 192.168.56.1:17500 > 255.255.255.255:17500 / Raw 0009 Ether / IP / UDP 192.168.56.1:17500 > 255.255.255.255:17500 / Raw
Capture CDP >>> p=sniff(iface=interface, count=2, filter="ether dst 01:00:0c:cc:cc:cc") >>> p <Sniffed: TCP:0 UDP:0 ICMP:0 Other:2> >>> p.display() 0000 802.3 08:00:27:c9:d5:7e > 01:00:0c:cc:cc:cc / LLC / SNAP / Raw 0001 802.3 08:00:27:c9:d5:7e > 01:00:0c:cc:cc:cc / LLC / SNAP / Raw
>>> p[0].display()
###[ 802.3 ]###
dst = 01:00:0c:cc:cc:cc
src = 08:00:27:c9:d5:7e
len = 386
###[ LLC ]###
dsap = 0xaa
ssap = 0xaa
ctrl = 3
###[ SNAP ]###
OUI = 0xc
code = 0x2000
###[ Raw ]###
load = '\x02\xb4\x91\x18\x00\x01\x00\x13CSR-A.lab.local\x00\x05\x01\x05Cisco IOS Software [Fuji], Virtual XE Software (X86_64_LINUX_IOSD-UNIVERSALK9-M), Version 16.9.1, RELEASE SOFTWARE (fc2)\nTechnical Support: http://www.cisco.com/techsupport\nCopyright (c) 1986-2018 by Cisco Systems, Inc.\nCompiled Tue 17-Jul-18 16:57 by mcpre\x00\x06\x00\x12cisco CSR1000V\x00\x02\x00\x11\x00\x00\x00\x01\x01\x01\xcc\x00\x04\xc0\xa88e\x00\x03\x00\x14GigabitEthernet2\x00\x04\x00\x08\x00\x00\x00!\x00\x07\x00\t\n\x00\x02\x00\x18\x00\x0b\x00\x05\x01\x00\x16\x00\x11\x00\x00\x00\x01\x01\x01\xcc\x00\x04\xc0\xa88e'
>>> list_contrib()
avs : AVS WLAN Monitor Header status=loads
bgp : BGP v0.1 status=loads
carp : CARP status=loads
cdp : Cisco Discovery Protocol status=loads
chdlc : Cisco HDLC and SLARP status=loads
coap : Constrained Application Protocol (CoAP) status=loads
diameter : Diameter status=loads
dtp : DTP status=loads
eigrp : EIGRP status=loads
etherip : EtherIP status=loads
gsm_um : PPI status=loads
gtp : GTP status=loads
gtp_v2 : GTPv2 status=loads
homeplugav : HomePlugAV Layer status=loads
http2 : HTTP/2 (RFC 7540, RFC 7541) status=loads
icmp_extensions : ICMP Extensions status=loads
igmp : IGMP/IGMPv2 status=loads
igmpv3 : IGMPv3 status=loads
ikev2 : IKEv2 status=loads
isis : ISIS status=loads
ldp : Label Distribution Protocol (LDP) status=loads
lldp : LLDP status=loads
macsec : - status=?
modbus : ModBus Protocol status=loads
mpls : MPLS status=loads
mqtt : - status=?
nsh : NSH Protocol status=loads
openflow : Openflow v1.0 status=loads
openflow3 : Openflow v1.3 status=loads
ospf : OSPF status=loads
pnio : ProfinetIO base layer status=loads
pnio_rtc : ProfinetIO Real-Time Cyclic (RTC) status=loads
ppi : PPI status=loads
ppi_cace : PPI CACE status=loads
ppi_geotag : PPI GEOLOCATION status=loads
ripng : RIPng status=loads
rsvp : RSVP status=loads
sebek : Sebek status=loads
send : Secure Neighbor Discovery (SEND) (ICMPv6) status=loads
skinny : Skinny Call Control Protocol (SCCP) status=loads
spbm : SBPM status=loads
tacacs : TACACS+ Protocol status=loads
tzsp : TZSP status=loads
ubberlogger : Ubberlogger dissectors status=loads
vqp : VLAN Query Protocol status=loads
vtp : VLAN Trunking Protocol (VTP) status=loads
wpa_eapol : WPA EAPOL dissector status=loads
>>> load_contrib("cdp")
>>> load_contrib("cdp")
>>> p=sniff(iface=interface, count=1, filter=capturefilter)
>>>
>>>
>>> p[0].show()
###[ 802.3 ]###
dst = 01:00:0c:cc:cc:cc
src = 08:00:27:c9:d5:7e
len = 386
###[ LLC ]###
dsap = 0xaa
ssap = 0xaa
ctrl = 3
###[ SNAP ]###
OUI = 0xc
code = 0x2000
###[ Cisco Discovery Protocol version 2 ]###
vers = 2
ttl = 180
cksum = 0x9118
\msg \
|###[ Device ID ]###
| type = Device ID
| len = 19
| val = 'CSR-A.lab.local'
|###[ Software Version ]###
| type = Software Version
| len = 261
| val = 'Cisco IOS Software [Fuji], Virtual XE Software (X86_64_LINUX_IOSD-UNIVERSALK9-M), Version 16.9.1, RELEASE SOFTWARE (fc2)\nTechnical Support: http://www.cisco.com/techsupport\nCopyright (c) 1986-2018 by Cisco Systems, Inc.\nCompiled Tue 17-Jul-18 16:57 by mcpre'
|###[ Platform ]###
| type = Platform
| len = 18
| val = 'cisco CSR1000V'
|###[ Addresses ]###
| type = Addresses
| len = 17
| naddr = 1
| \addr \
| |###[ CDP Address IPv4 ]###
| | ptype = NLPID
| | plen = 1
| | proto = '\xcc'
| | addrlen = 4
| | addr = 192.168.56.101
|###[ Port ID ]###
| type = Port ID
| len = 20
| iface = 'GigabitEthernet2'
|###[ Capabilities ]###
| type = Capabilities
| len = 8
| cap = Router+IGMPCapable
|###[ IP Prefix ]###
| type = IP Prefix
| len = 9
| defaultgw = 10.0.2.0
|###[ CDP Generic Message ]###
| type = 0x1800
| len = 2816
| val = '\x05\x01\x00\x16\x00\x11\x00\x00\x00\x01\x01\x01\xcc\x00\x04\xc0\xa88e'
>>> device=p[0]["CDPMsgDeviceID"].val.decode()
>>> device
'CSR-A.lab.local'
>>> hostname=device.split(".")[0]
>>> hostname
'CSR-A'
>>> ip=p[0]["CDPAddrRecordIPv4"] >>> ip.addr '192.168.56.101'
To enable immediate remote-access to brandnew deployed virtual Cisco CSR1000V-Routers by scripts, ansible etc. it’s necessary to predeploy the startup-config at least with public-rsa-keys etc.
Download and install the nice tool http://CDBurnerXP. This will install a companion cli-tool cdbxpcmd.exe along with the GUI-Version.
It’ll be used to prepare an ISO-„CDROM“ containing the prepared „startup-config“-file.
Prepare an IOS-XE Configuration file…
! hostname HOSTNAME ! ... ! ! platform console serial ! crypto key generate rsa modulus 2048 label RSA_SSH ! ! username labuser privilege 15 ! ip ssh pubkey-chain ! username labuser key-string ... exit exit ! exit ! ... ! ip ssh rsa keypair-name RSA_SSH ! ip ssh server algorithm authentication publickey ! ... ! line vty 0 15 login local transport input ssh access-class ACL_NMM in vrf-also ! end
These commands create the ISO-File in the %LOC%-Path.
set VM=CSR1000vX ... : Create ISO containing slipstreamed config-file : use UNXTOOLS "sed" to customize the "hostname"-Command : set CFGISO=%LOC%\config.iso set CFGSRC=C:\RH\LAB\VM\iosxe_config.txt set CFGTXT=%LOC%\iosxe_config.txt cat %CFGSRC% | sed "s/HOSTNAME/%VM%/g" > %CFGTXT% "%ProgramFiles(x86)%"\CDBurnerXP\cdbxpcmd.exe --burn-data -file:%CFGTXT% -iso:%CFGISO% -format:iso
The contained config-file will get automatically applied when the router boots the first time.
VBoxManage storageattach %VM% --storagectl IDE-CTL --port 1 --device 1 --type dvddrive --medium %CFGISO%
This depends of the configuration-file, of course.
In a lab environment it might be handy to quickly rollout new (virtual) routers without much manual intervention. The following script creates a VirtualBox-VM and boots it up.
Install VirtualBox and have a CSR1000V-ISO-File ready.
set VM=CSR1000V set BASE=c:\RH\LAB\VM set ISO=C:\Downloads\csr1000v-universalk9.16.09.01.iso : Create VM VBoxManage createvm --name %VM% --ostype "Linux26_64" --basefolder %BASE% --register !:now the Path in the Filesystem to ...LOC... exists set LOC=%BASE%\%VM% : Customize VM VBoxManage modifyvm %VM% --memory 4096 VBoxManage modifyvm %VM% --vram 16 VBoxManage modifyvm %VM% --pae on --paravirtprovider default --hwvirtex on --nestedpaging on : Storage VBoxManage createhd --filename %LOC%\%VM%.vdi --size 8192 VBoxManage storagectl %VM% --name "IDE-CTL" --add ide --portcount 2 --bootable on VBoxManage storageattach %VM% --storagectl IDE-CTL --port 0 --device 0 --type hdd --medium %LOC%\%VM%.vdi VBoxManage storageattach %VM% --storagectl IDE-CTL --port 1 --device 0 --type dvddrive --medium %ISO% VBoxManage modifyvm %VM% --boot1=dvd --boot2=disk --boot3=none --boot4=none : Serial-Interfaces via "Pipe" VBoxManage modifyvm %VM% --uartmode1 server \\.\pipe\%VM% VBoxManage modifyvm %VM% --uart1 0x3f8 4 VBoxManage modifyvm %VM% --uartmode2 server \\.\pipe\%VM%_diag VBoxManage modifyvm %VM% --uart2 0x2f8 4 : Audio VBoxManage modifyvm %VM% --audio none : NICs VBoxManage modifyvm %VM% --nic1 nat --nic2 hostonly --nic3 hostonly --nic4 hostonly VBoxManage modifyvm %VM% --nictype1 virtio --nictype2 virtio --nictype3 virtio --nictype4 virtio VBoxManage modifyvm %VM% --nicpromisc1 allow-all --nicpromisc2 allow-all --nicpromisc3 allow-all --nicpromisc4 allow-all VBoxManage modifyvm %VM% --hostonlyadapter2 "VirtualBox Host-Only Ethernet Adapter" VBoxManage modifyvm %VM% --hostonlyadapter3 "VirtualBox Host-Only Ethernet Adapter" VBoxManage modifyvm %VM% --hostonlyadapter4 "VirtualBox Host-Only Ethernet Adapter" : Set the VM-Logo for the VirtualBox-Inventory VBoxManage modifyvm %VM% --iconfile C:\RH\LAB\72px-Cisco_logo.svg.png : Boot the VM, it'l reboot once to apply the running-config VBoxManage startvm %VM%
conf t platform console serial end
After another reboot the serial console can be accessed by a windows pipe:
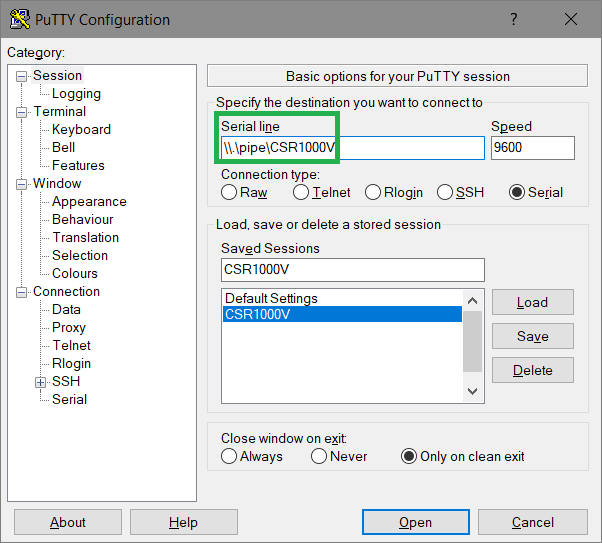
It’s a two step process to get rid of insecure username/password-authentication.
btw. Cisco-IOS doesn’t support DSA-keys
This user-account could get privileges from a Radius/TACACS+-Server which could provide access-logs, too.
I prefer Putty, usually in form of „mRemoteNG“, so i use PuttyGen to generate the RSA keypair.
C:>dir labuser*.* -l -rw-rw-rw- 1 user group 2710 Oct 17 18:26 labuser.ppk -rw-rw-rw- 1 user group 820 Oct 17 18:26 labuser.pub
C:>cat labuser.pub ---- BEGIN SSH2 PUBLIC KEY ---- Comment: "labuser" AAAAB3NzaC1yc2EAAAABJQAAAgEAg+0v9spZ0ZaBmgK3eVWJmY1Q4bNYcuY/uZDn c0JFPXgn9dA5r44GksqIEpYjkbMZf61Nkwazz4Cfxw4byS/HeajYP8Rs/eWXV6dh k829tqvqSLN6TwH+v49MllGpiHbiVGyoRvzfPgUVddN1j8cMEIJHgVJk4AS4fJmx Mp+2wMFWGldJ5xlUaOXO+XaOaTlAFYimgdYNbO7x4+vMRtrqp3ORJJZ5Tdf0JuFp cUHRlV46e2FL1FZ8p2PDLVUiAlg8o8yxI8D52r0A5VQToKz3wKUchTWIWqRmIfOR fS5jJz8+yTb/swkFs4FzAEpxD8CgvArz7ewTkna0zm8/wbysZCH1lKyce7AmZCp9 lm1Nsythl+6ztB9M01AbzBo2ElVo3GZHEr3AclsON8aCKgf8hVaZww5BqN1YHvUj dKH0Mb8i0zLs+XFSgV7rYXg1EcHyBqsRFAi5OdkuGwd5D2NfWkcwk2XBsi6qG8bP 951MlHi0SuiMTSTmskdf1OyzzIFaPYjaW9VQe36tg07MsBP48KOPEB4803k35gWx Sw2nxAO4O9KisYNCfw0SHna9RiAWRsyykLUTe6Z39vzppTEiC+j2f6IQs9Celk4S s9r8IIoI0yswtvc/DsJBLd8y0CmNwyZof9L5MSY1RlcBiCykUPh1Z+UFLEYrFBa1 qQCAwU8= ---- END SSH2 PUBLIC KEY ----
C:>egrep "^[a-zA-Z0-9+\/=]+$" labuser.pub AAAAB3NzaC1yc2EAAAABJQAAAgEAg+0v9spZ0ZaBmgK3eVWJmY1Q4bNYcuY/uZDn c0JFPXgn9dA5r44GksqIEpYjkbMZf61Nkwazz4Cfxw4byS/HeajYP8Rs/eWXV6dh k829tqvqSLN6TwH+v49MllGpiHbiVGyoRvzfPgUVddN1j8cMEIJHgVJk4AS4fJmx Mp+2wMFWGldJ5xlUaOXO+XaOaTlAFYimgdYNbO7x4+vMRtrqp3ORJJZ5Tdf0JuFp cUHRlV46e2FL1FZ8p2PDLVUiAlg8o8yxI8D52r0A5VQToKz3wKUchTWIWqRmIfOR fS5jJz8+yTb/swkFs4FzAEpxD8CgvArz7ewTkna0zm8/wbysZCH1lKyce7AmZCp9 lm1Nsythl+6ztB9M01AbzBo2ElVo3GZHEr3AclsON8aCKgf8hVaZww5BqN1YHvUj dKH0Mb8i0zLs+XFSgV7rYXg1EcHyBqsRFAi5OdkuGwd5D2NfWkcwk2XBsi6qG8bP 951MlHi0SuiMTSTmskdf1OyzzIFaPYjaW9VQe36tg07MsBP48KOPEB4803k35gWx Sw2nxAO4O9KisYNCfw0SHna9RiAWRsyykLUTe6Z39vzppTEiC+j2f6IQs9Celk4S s9r8IIoI0yswtvc/DsJBLd8y0CmNwyZof9L5MSY1RlcBiCykUPh1Z+UFLEYrFBa1 qQCAwU8=
$ cd ~/.ssh/ $ ls -l total 20 -rw------- 1 administrator administrator 1675 Aug 28 09:43 id_rsa -rw-r--r-- 1 administrator administrator 405 Aug 28 09:43 id_rsa.pub -rw-r--r-- 1 administrator administrator 222 Aug 28 11:07 known_hosts
$ cat id_rsa.pub ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCohMsS3gJ/OcF4Hg43mKeVHKWl2lECCn0iZQu9QSrUjAb4PVHWXIbj11yy5Jh/ygMys0n9IED6357fkRmq8Cc8ujpU0sCen7kBFUt3UqbLg1PLT9wMmJAEv4dcxbX9WRvwYXjLd8+EgDYDmrj7vTB3xIvw1I2WWuUK2jPWbVI57vbyGtw224Qb9Qk0KQfyGiTvErZnddDg65/rn9Pyt7FQlzCwUPH0nyJVoFhiYYJYJszTKc8BTFB6VdIbALHc4atFmjYt7YDUvEvaZqOL+zwQtr7FmXsZ5oaRGV6ZChuBPTpNEL41w/Il1mSJicRykpD90O2AxlUFebQfABTWadnr administrator@lx-ubuntu
The RFC states that the key should get split into multiple lines containing max. 72 characters.
$ cut -d " " -f 2 id_rsa.pub AAAAB3NzaC1yc2EAAAADAQABAAABAQCohMsS3gJ/OcF4Hg43mKeVHKWl2lECCn0iZQu9QSrUjAb4PVHWXIbj11yy5Jh/ygMys0n9IED6357fkRmq8Cc8ujpU0sCen7kBFUt3UqbLg1PLT9wMmJAEv4dcxbX9WRvwYXjLd8+EgDYDmrj7vTB3xIvw1I2WWuUK2jPWbVI57vbyGtw224Qb9Qk0KQfyGiTvErZnddDg65/rn9Pyt7FQlzCwUPH0nyJVoFhiYYJYJszTKc8BTFB6VdIbALHc4atFmjYt7YDUvEvaZqOL+zwQtr7FmXsZ5oaRGV6ZChuBPTpNEL41w/Il1mSJicRykpD90O2AxlUFebQfABTWadnr $ cut -d " " -f 2 id_rsa.pub | fold -b -w 72 AAAAB3NzaC1yc2EAAAADAQABAAABAQCohMsS3gJ/OcF4Hg43mKeVHKWl2lECCn0iZQu9QSrU jAb4PVHWXIbj11yy5Jh/ygMys0n9IED6357fkRmq8Cc8ujpU0sCen7kBFUt3UqbLg1PLT9wM mJAEv4dcxbX9WRvwYXjLd8+EgDYDmrj7vTB3xIvw1I2WWuUK2jPWbVI57vbyGtw224Qb9Qk0 KQfyGiTvErZnddDg65/rn9Pyt7FQlzCwUPH0nyJVoFhiYYJYJszTKc8BTFB6VdIbALHc4atF mjYt7YDUvEvaZqOL+zwQtr7FmXsZ5oaRGV6ZChuBPTpNEL41w/Il1mSJicRykpD90O2AxlUF ebQfABTWadnr
$ ssh-keygen -t rsa -b 4096 Generating public/private rsa key pair. Enter file in which to save the key (/home/administrator/.ssh/id_rsa): newid_rsa Enter passphrase (empty for no passphrase): ***** Enter same passphrase again: ***** Your identification has been saved in newid_rsa. Your public key has been saved in newid_rsa.pub. The key fingerprint is: SHA256:4g/JkvpFQmlTaOE2VQAZ9IHfz/+6NJiI8W/WVt9TJGA administrator@lx-ubuntu The key's randomart image is: +---[RSA 4096]----+ | .=B=o. | | .== . E | | .O... . . | | + o. . . .| | . + So o | | * * .oo . .| | o B o ooo. .o| | . o o .o.+. .o| | ... .o..o+. .| +----[SHA256]-----+ $ ls -l total 36 ... -rw------- 1 administrator administrator 3326 Oct 18 07:19 newid_rsa -rw-r--r-- 1 administrator administrator 749 Oct 18 07:19 newid_rsa.pub
conf t ip ssh pubkey-chain username labuser key-string AAAAB3NzaC1yc2EAAAABJQAAAgEAg+0v9spZ0ZaBmgK3eVWJmY1Q4bNYcuY/uZDn c0JFPXgn9dA5r44GksqIEpYjkbMZf61Nkwazz4Cfxw4byS/HeajYP8Rs/eWXV6dh k829tqvqSLN6TwH+v49MllGpiHbiVGyoRvzfPgUVddN1j8cMEIJHgVJk4AS4fJmx Mp+2wMFWGldJ5xlUaOXO+XaOaTlAFYimgdYNbO7x4+vMRtrqp3ORJJZ5Tdf0JuFp cUHRlV46e2FL1FZ8p2PDLVUiAlg8o8yxI8D52r0A5VQToKz3wKUchTWIWqRmIfOR fS5jJz8+yTb/swkFs4FzAEpxD8CgvArz7ewTkna0zm8/wbysZCH1lKyce7AmZCp9 lm1Nsythl+6ztB9M01AbzBo2ElVo3GZHEr3AclsON8aCKgf8hVaZww5BqN1YHvUj dKH0Mb8i0zLs+XFSgV7rYXg1EcHyBqsRFAi5OdkuGwd5D2NfWkcwk2XBsi6qG8bP 951MlHi0SuiMTSTmskdf1OyzzIFaPYjaW9VQe36tg07MsBP48KOPEB4803k35gWx Sw2nxAO4O9KisYNCfw0SHna9RiAWRsyykLUTe6Z39vzppTEiC+j2f6IQs9Celk4S s9r8IIoI0yswtvc/DsJBLd8y0CmNwyZof9L5MSY1RlcBiCykUPh1Z+UFLEYrFBa1 qQCAwU8= exit username labuser key-string AAAAB3NzaC1yc2EAAAADAQABAAABAQCohMsS3gJ/OcF4Hg43mKeVHKWl2lECCn0iZQu9QSrU jAb4PVHWXIbj11yy5Jh/ygMys0n9IED6357fkRmq8Cc8ujpU0sCen7kBFUt3UqbLg1PLT9wM mJAEv4dcxbX9WRvwYXjLd8+EgDYDmrj7vTB3xIvw1I2WWuUK2jPWbVI57vbyGtw224Qb9Qk0 KQfyGiTvErZnddDg65/rn9Pyt7FQlzCwUPH0nyJVoFhiYYJYJszTKc8BTFB6VdIbALHc4atF mjYt7YDUvEvaZqOL+zwQtr7FmXsZ5oaRGV6ZChuBPTpNEL41w/Il1mSJicRykpD90O2AxlUF ebQfABTWadnr exit exit exit end
VBOX-CSR-1#show run | section key-chain ip ssh pubkey-chain username labuser key-hash ssh-rsa CE7178C1D6D025F7EA5345CCBA22ED54 key-hash ssh-rsa ABBF42AB330CA79B235FB369FCC4D53E
ssh-rsa 4096 ce:71:78:c1:d6:d0:25:f7:ea:53:45:cc:ba:22:ed:54
so you could save time to just configure the hash.
$ who administrator pts/0 Oct 18 17:37 (192.168.56.1)
Linux re-uses the name of the current linux-user to login into the ssh-device unless a user is specified
$ ssh 192.168.56.102 Password:
The IOS-Router prompts for a password for users who have no known-public-key in the running-config – and there is no public-key for a user named „administrator“.
(config)# ip ssh server algorithm authentication publickey keyboard password
conf t ip ssh server algorithm authentication publickey end
$ ssh 192.168.56.102 administrator@192.168.56.102: Permission denied (publickey).
$ ssh -l labuser 192.168.56.102
VBOX-CSR-1>who
Line User Host(s) Idle Location
0 con 0 idle 00:02:43
* 1 vty 0 labuser idle 00:00:00 192.168.56.101
VBOX-CSR-1>enable % No password set
conf t username labuser privilege 15 end
$ ssh -l labuser 192.168.56.102
VBOX-CSR-1#who
Line User Host(s) Idle Location
0 con 0 idle 00:00:10
* 1 vty 0 labuser idle 00:00:00 192.168.56.101
Interface User Mode Idle Peer Address
VBOX-CSR-1#show priv
Current privilege level is 15
[btw. the linux-ssh-client „labuser“ is still logged in]
That’s all.
…this article should have been published at 2017-11-23, i forgot to press the right botton.
So, an update might be needed, anyone still interested in cot today?
Release 2.1 (2018-01-29) is the current release, containing some fixes (https://github.com/glennmatthews/cot/blob/master/CHANGELOG.rst)
So, let’s go, following
administrator@lx-ubuntu:~$ sudo pip install cot
sudo: pip: command not found
thats embarassing.
Install PIP first
$ sudo apt-get update
$ sudo apt-get install python-pip
$ pip --version
pip 9.0.1 from /usr/lib/python2.7/dist-packages (python 2.7)
Try it again
$ sudo pip install cot
...
Successfully installed backports.shutil-get-terminal-size-1.0.0 colorlog-3.1.4 cot-2.1.0 ndg-httpsclient-0.5.1 pyvmomi-6.7.0.2018.9 verboselogs-1.7
$ cot --version
Common OVF Tool (COT), version 2.1.0
Copyright (C) 2013-2017 the COT project developers.
Not essential, but handy.
$sudo pip install argcomplete
...
Successfully installed argcomplete-1.9.4
A full installation requires so called „cot-helpers“ to use all features.
$ cot install-helpers --verify-only
Results:
-------------
COT manpages: DIRECTORY NOT FOUND: /usr/local/man/man1
fatdisk: NOT FOUND
mkisofs: NOT FOUND
ovftool: NOT FOUND
qemu-img: NOT FOUND
vmdktool: NOT FOUND
$ sudo apt-get install xutils-dev
...
Setting up xutils-dev (1:7.7+5ubuntu1) ...
$ sudo cot install-helpers
...
Results:
-------------
COT manpages: already installed, no updates needed
fatdisk: INSTALLATION FAILED: [Errno 1] Helper program './RUNME' exited with error 1
mkisofs: version 2.1, present at /usr/bin/mkisofs
ovftool: INSTALLATION FAILED: No support for automated installation of ovftool, as VMware requires a site login to
download it. See https://www.vmware.com/support/developer/ovf/
qemu-img: version 2.11.1, present at /usr/bin/qemu-img
vmdktool: version 1.4, present at /usr/local/bin/vmdktool
[Errno 1] Unable to install some helpers
first fix „fatdisk“ which is used to inject configs into OVA-Files
$ sudo cp /usr/include/x86_64-linux-gnu/bits/stdint-intn.h /usr/include/x86_64-linux-gnu/bits/stdint-intn.h.bak
$ sudo vi /usr/include/x86_64-linux-gnu/bits/stdint-intn.h
uncomment
typedef __int64_t int64_t;
to
//typedef __int64_t int64_t;
and run the helper-installation again:
$ sudo cot install-helpers
...
NOTICE : Successfully installed 'fatdisk'
Results:
-------------
COT manpages: already installed, no updates needed
fatdisk: successfully installed to /usr/local/bin/fatdisk, version 1.0
mkisofs: version 2.1, present at /usr/bin/mkisofs
ovftool: INSTALLATION FAILED: No support for automated installation of ovftool, as VMware requires a site login to
download it. See https://www.vmware.com/support/developer/ovf/
qemu-img: version 2.11.1, present at /usr/bin/qemu-img
vmdktool: version 1.4, present at /usr/local/bin/vmdktool
[Errno 1] Unable to install some helpers
But it threw a lot of warnings..
warning: format ‘%lu’ expects argument of type ‘long unsigned int’, but argument 3 has type ‘int64_t {aka long long int}’ [-Wformat=]
… but it compiles… Memo: Try manual compilation…
$ mkdir fatdisk
$ cd fatdisk
$ wget -O fatdisk.tgz https://github.com/goblinhack/fatdisk/archive/master.tar.gz
$ tar zxf fatdisk.tgz
$ cd fatdisk-master/
$ ./RUNME
OFVTool of course has to be installed manually
Download from VMware: OVFTOOL-Download
Upload to the Linux-Server using Putty-SCP(PSCP) and public-key-authentication:
C:\Downloads>pscp -scp -i C:\rh.priv.ppk VMware-ovftool-4.3.0-7948156-lin.x86_64.bundle administrator@192.168.56.101:
VMware-ovftool-4.3.0-7948 | 35623 kB | 35623.9 kB/s | ETA: 00:00:00 | 100%
At the Linux-Server
$ ls -l
total 35644
-rw-r--r-- 1 administrator administrator 36478864 Oct 15 18:36 VMware-ovftool-4.3.0-7948156-lin.x86_64.bundle
$ chmod a+x VMware-ovftool-4.3.0-7948156-lin.x86_64.bundle
$ sudo ./VMware-ovftool-4.3.0-7948156-lin.x86_64.bundle
...
Installing VMware OVF Tool component for Linux 4.3.0
Configuring...
[######################################################################] 100%
Installation was successful.
administrator@lx-ubuntu:~$ cot install-helpers --verify-only
Results:
-------------
COT manpages: already installed, no updates needed
fatdisk: version 1.0, present at /usr/local/bin/fatdisk
mkisofs: version 2.1, present at /usr/bin/mkisofs
ovftool: version 4.3, present at /usr/bin/ovftool
qemu-img: version 2.11.1, present at /usr/bin/qemu-img
vmdktool: version 1.4, present at /usr/local/bin/vmdktool
The CSR1000V-Router has already been prepared (Create a CSR1000V-Instance with nested Virtualiation support) and in (Part 4: Package the Service-VM into an OVA) we copied the OVA-Image of our „ubuntu-server“-VM to this Router.
Add the internal Network-Interface between Router and Service-VM
SERVICECONTAINER#conf t Enter configuration commands, one per line. End with CNTL/Z. SERVICECONTAINER(config)#int virtualportgroup 0 *Feb 3 19:05:17.206: %LINEPROTO-5-UPDOWN: Line protocol on Interface VirtualPortGroup0, changed state to up SERVICECONTAINER(config-if)#ip addr 192.168.0.1 255.255.255.0 SERVICECONTAINER(config-if)#exit SERVICECONTAINER(config)#virtual-service SERVICECONTAINER(config-virt-serv-global)#signing level unsigned % Support for unsigned packages has been user-enabled. Unsigned packages are not endorsed by Cisco Systems, Inc. User assumes all responsibility SERVICECONTAINER(config-virt-serv-global)#ex SERVICECONTAINER(config)#ip dhcp pool SERVICE SERVICECONTAINER(dhcp-config)# network 192.168.0.0 255.255.255.0 SERVICECONTAINER(dhcp-config)# exit SERVICECONTAINER(config)#virtual-service UBUNTU SERVICECONTAINER(config-virt-serv)#vnic gateway virtualPortGroup 0 SERVICECONTAINER(config-virt-serv-vnic)#guest ip address 192.168.0.2 SERVICECONTAINER(config-virt-serv-vnic)#end SERVICECONTAINER# *Feb 3 19:06:27.474: %SYS-5-CONFIG_I: Configured from console by console
Install the Service-VM
SERVICECONTAINER#debug virtual-service all virtual service all debugging is on SERVICECONTAINER#term mon % Console already monitors SERVICECONTAINER#term width 0
SERVICECONTAINER#virtual-service install name UBUNTU package bootflash:ubuntu1604.ova Installing package 'bootflash:/ubuntu1604.ova' for virtual-service 'UBUNTU'. Once the install has finished, the VM may be activated. Use 'show virtual-service list' for progress. *Feb 3 19:07:43.518: VIRTUAL-SERVICE [UBUNTU]: Sending install req for [UBUNTU], path=bootflash:/ubuntu1604.ova, uri= uid=0 *Feb 3 19:07:43.529: VIRTUAL-INSTANCE: Message sent for INSTALL TDL request: Virtual-instance name: UBUNTU, UID: 0 *Feb 3 19:07:43.529: VIRTUAL-SERVICE: Started response timer for tid DD000001 - 30 minutes *Feb 3 19:05:14.205: %IOSXE-4-PLATFORM: R0/0: kernel: dev->name [intsvc0]: dev_entry not populated SERVICECONTAINER#show virtual-service list System busy installing virtual-service 'UBUNTU'. The request may take several minutes... Virtual Service List: Name Status Package Name ------------------------------------------------------------------------------ UBUNTU Installing ubuntu1604.ova *Feb 3 19:08:00.645: %VMAN-5-PACKAGE_SIGNING_LEVEL_ON_INSTALL: R0/0: vman: Package 'ubuntu1604.ova' for service container 'UBUNTU' is 'unsigned', signing level cached on original install is 'unsigned' *Feb 3 19:08:09.216: VIRTUAL-SERVICE: Install response handler: VM[UBUNTU]: Owner IOSd trans_id 3707764737 *Feb 3 19:08:09.216: VIRTUAL-SERVICE [UBUNTU]: vm[UBUNTU] set owner [IOSd] *Feb 3 19:08:09.225: VIRTUAL-SERVICE [UBUNTU]: application_name: 'ubuntu' application_vendor: '' application_version: '1.1' *Feb 3 19:08:09.226: VIRTUAL-SERVICE [UBUNTU]: Default profile info: license_name: '', license_ver: '' *Feb 3 19:08:09.226: VIRTUAL-SERVICE: Install pkg response for tid DD000001: rc=0, descr=Install Success *Feb 3 19:08:09.226: VIRTUAL-SERVICE [UBUNTU]: License type: none, no license needed *Feb 3 19:08:09.226: %VIRT_SERVICE-5-INSTALL_STATE: Successfully installed virtual service UBUNTU *Feb 3 19:08:09.243: VIRTUAL-SERVICE: Received local transport activation request *Feb 3 19:08:09.244: VIRTUAL-SERVICE: Enabling vman local transport SERVICECONTAINER#show virtual-service list Virtual Service List: Name Status Package Name ------------------------------------------------------------------------------ UBUNTU Installed ubuntu1604.ova *Feb 3 19:08:32.758: %ONEP_BASE-6-SS_ENABLED: ONEP: Service set Base was enabled by Default *Feb 3 19:08:33.259: VIRTUAL-SERVICE: Local transport 'activation' request processed
Activate the installed Service-VM
SERVICECONTAINER#conf t
Enter configuration commands, one per line. End with CNTL/Z.
SERVICECONTAINER(config)#virtual-service UBUNTU
SERVICECONTAINER(config-virt-serv)#activate
SERVICECONTAINER(config-virt-serv)#end
% Activating virtual-service 'UBUNTU', this might take a few minutes. Use 'show virtual-service list' for progress.
*Feb 3 19:09:57.772: VIRTUAL-SERVICE [UBUNTU]: Activate CLI: appl->owner [IOSd]
*Feb 3 19:09:57.775: VIRTUAL-INSTANCE: Message sent for ACTIVATE TDL request: Virtual service name: UBUNTU, UID: 0
*Feb 3 19:09:57.775: VIRTUAL-SERVICE [UBUNTU]: Started virtual service (0) activate response timer - 30 minutes
*Feb 3 19:10:06.052: %SYS-5-CONFIG_I: Configured from console by console
*Feb 3 19:10:06.383: VIRTUAL-SERVICE [UBUNTU]: Activate response handler: got owner [IOSd]
*Feb 3 19:10:06.383: VIRTUAL-SERVICE: clnt_type 0: Interface counter is '1'
*Feb 3 19:10:06.383: VIRTUAL-SERVICE: Information for virtual port grp '0' is received
*Feb 3 19:10:06.384: VIRTUAL-SERVICE [UBUNTU]: Deliver intf response, vm =UBUNTU, counter=1
*Feb 3 19:10:06.384: VIRTUAL-SERVICE [UBUNTU]: Received interface id=0, type=1, state=1
*Feb 3 19:10:06.384: VIRTUAL-SERVICE [UBUNTU]: Received virtual port group interface 0 with service MAC 001e.e5b1.cfba, state: up
*Feb 3 19:10:06.385: VIRTUAL-INSTANCE: Message sent for IF MTU TDL message: appliance 'UBUNTU'
*Feb 3 19:10:06.385: VIRTUAL-SERVICE [UBUNTU]: Activate response handler: rsp_rc 0
*Feb 3 19:10:06.385: VIRTUAL-SERVICE [UBUNTU]: Deliver response: appliance_state 3 rsp_rc 0 if_notify name UBUNTU clnt_type 0 act_state 0
*Feb 3 19:10:06.385: %VIRT_SERVICE-5-ACTIVATION_STATE: Successfully activated virtual service UBUNTUconf t
*Feb 3 19:10:06.385: VIRTUAL-SERVICE [UBUNTU]: Stopped virtual service (1) response timer
*Feb 3 19:10:06.385: VIRTUAL-SERVICE: Delivered Virt-manager response message to virtual service 'UBUNTU' - Response: 'OK'
*Feb 3 19:10:06.385: VIRTUAL-SERVICE [UBUNTU]: set owner to 'IOSd' in appliance
SERVICECONTAINER#show virtual-service list
Virtual Service List:
Name Status Package Name
------------------------------------------------------------------------------
UBUNTU Activated ubuntu1604.ova
SERVICECONTAINER#show ip dhcp bind
Bindings from all pools not associated with VRF:
IP address Client-ID/ Lease expiration Type State Interface
Hardware address/
User name
192.168.0.2 001e.e5b1.cfba Feb 04 2018 07:20 PM Automatic Active VirtualPortGroup0
Access the VM using the (virtual) Serial-Console
SERVICECONTAINER#virtual-service connect name UBUNTU console Connected to appliance. Exit using ^c^c^c Ubuntu 16.04.3 LTS ubuntu-server ttyS0 ubuntu-server login: user Password: Last login: Sat Feb 3 20:23:27 CET 2018 on ttyS0 Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.4.0-87-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 9 packages can be updated. 7 updates are security updates. user@ubuntu-server:~$ who user ttyS0 2018-02-03 23:12
Logout: 3x [CTRL]+
user@ubuntu-server:~$ ^C user@ubuntu-server:~$ ^C user@ubuntu-server:~$ ^C
Access the VM using SSH via the internal Network
SERVICECONTAINER#ssh -l user 192.168.0.2 Password: Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.4.0-87-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 9 packages can be updated. 7 updates are security updates. Last login: Sat Feb 3 23:12:21 2018 user@ubuntu-server:~$ who user pts/0 2018-02-03 23:13 (192.168.0.1)
Check the local python/NAPALM-Setup to get facts about the containing router
user@ubuntu-server:~$ python
Python 2.7.12 (default, Dec 4 2017, 14:50:18)
[GCC 5.4.0 20160609] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> import napalm
>>> iosdriver = napalm.get_network_driver('ios')
dpass', optional_args={'port': 22, 'dest_file_system': 'bootflash:'})sword='rmon
>>> router.open()
>>> print router.get_facts()
{u'os_version': u'Virtual XE Software (X86_64_LINUX_IOSD-UNIVERSALK9-M), Version 16.7.1, RELEASE SOFTWARE (fc6)', u'uptime': 12840, u'interface_list': [u'GigabitEthernet1', u'GigabitEthernet2', u'GigabitEthernet3', u'VirtualPortGroup0'], u'vendor': u'Cisco', u'serial_number': u'9SNHUBYAML', u'model': u'CSR1000V', u'hostname': u'SERVICECONTAINER', u'fqdn': u'SERVICECONTAINER.lab.local'}