about:config
browser.download.alwaysOpenPanel
switch to „false“
networking, computing, virtualization, automation
about:config
browser.download.alwaysOpenPanel
switch to „false“
everybody knows about IPv6 „2001:db8“ – but about the IPv4 pendants?
The blocks
are provided for use in documentation.
The „refreshenv“-CMD/Powershell-Command updates all Environment-Variables e.g. after installing a new software package.
C:\WINDOWS\system32>refreshenv
Refreshing environment variables from registry for cmd.exe. Please wait...Finished..
Both Protocols are absolutely useless for all common use-cases, but enabled – just „providing“ potential security issues.
Disable like this:
netsh interface isatap set state disabled
netsh interface teredo set state disabled
The Web is full of explanations, how to use „Cloud-Init Datasource for VMware GuestInfo“ but https://github.com/vmware-archive/cloud-init-vmware-guestinfo it is deprecated.
Cloud-Init 21.3 has been released https://discourse.ubuntu.com/t/release-of-cloud-init-21-3/23857 which integrates this software.
New name:
I’d expect it to be in the current Ubuntu 21.10 (Impish Indri) https://cloud-images.ubuntu.com/impish/current/ – the release notes for 21.10 don’t specify the exact version.
Ubuntu 20.04 (Focal Fossa) is still at cloud-init 20.1-10 according to https://wiki.ubuntu.com/FocalFossa/ReleaseNotes which is too old.
Unfortunately Ubuntu provides the „cloud“-images in OVA-Format.
Deploy
as
This shouldn’t be done manually, I’d suggest using terraform
Release 21.3 is available:
ubuntu@ubuntu:~$ cloud-init --version
/usr/bin/cloud-init 21.3-1-g6803368d-0ubuntu3
Datasource „vmware“ is included:
ubuntu@ubuntu:~$ cloud-id
vmware
I prefer accessing VMs using SSH or RDP directly. Sometimes, the IP-Address of the VM isn’t reachable, or protocols for remoteaccess need to be disabled for security reasons.
In these cases, if an IP-connection to the ESXi-Server is available this could be an option to use the ESXi hypervisor as VNC-Server to provide access to VM keyboard, video, mouse…
Three VM advanced Configuration Parameters need to be set:
RemoteDisplay.vnc.enabled = TRUE
RemoteDisplay.vnc.port = <TCP-Port>
RemoteDisplay.vnc.password = <Passwort>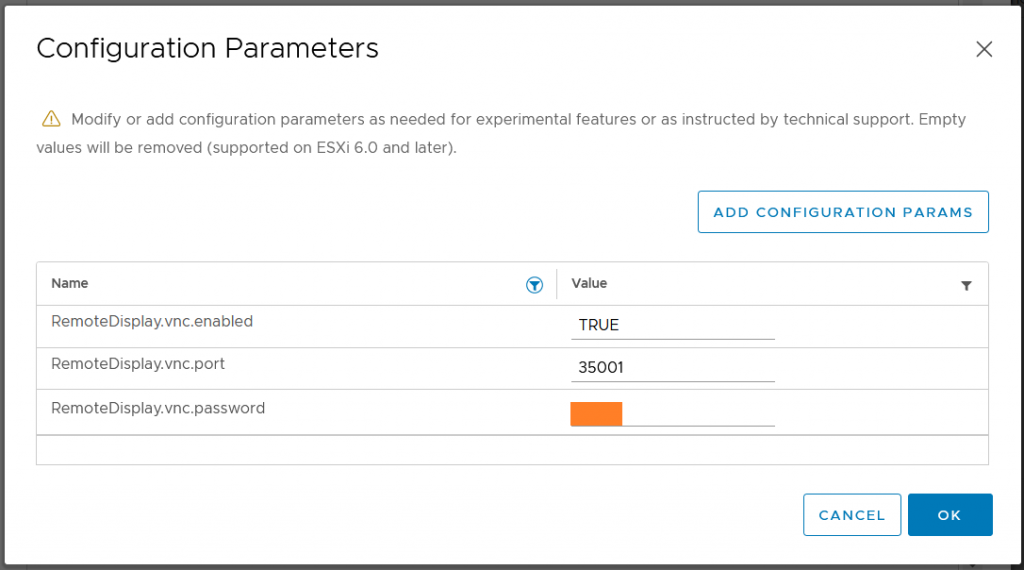
Terraform is a single .EXE-File so installation is about adding it’s folder to the $PATH-Variable and upgrading is about replacing „terraform.exe“ by the current version.
C:\RH\LAB\TERRAFORM\vSphere_N9K>terraform --version
Terraform v0.15.2
on windows_amd64
Your version of Terraform is out of date! The latest version
is 1.0.11. You can update by downloading from https://www.terraform.io/downloads.html
C:\dir "c:\Program Files (exe)"\terraform*.*
Volume in drive C is Windows
Volume Serial Number is 583C-0C08
Directory of c:\Program Files (exe)
05.05.2021 22:34 81.442.168 terraform.exe
1 File(s) 81.442.168 bytes
0 Dir(s) 8.344.129.536 bytes free
Download the current release („terraform_1.0.11_windows_amd64.zip“) unzip it and copy it to the correct destination:
C:\>dir "c:\Program Files (exe)"\terraform*.*
Volume in drive C is Windows
Volume Serial Number is 583C-0C08
Directory of c:\Program Files (exe)
12.11.2021 17:41 60.838.776 terraform.exe
05.05.2021 22:34 81.442.168 terraform.bak
2 File(s) 227.786.808 bytes
0 Dir(s) 8.344.129.536 bytes free
C:\terraform --version
Terraform v1.0.11
on windows_amd64
Using this „.tf“-File referencing the „hashicorp/vsphere“-Provider:
terraform {
required_version = ">= 0.13"
required_providers {
vsphere = {
source = "hashicorp/vsphere"
}
}
}
and initialize the project with current provider(s):
C:\>terraform init -upgrade
Initializing the backend...
Initializing provider plugins...
- Finding latest version of hashicorp/vsphere...
- Installing hashicorp/vsphere v2.0.2...
- Installed hashicorp/vsphere v2.0.2 (signed by HashiCorp)
Terraform has created a lock file .terraform.lock.hcl to record the provider
selections it made above. Include this file in your version control repository
so that Terraform can guarantee to make the same selections by default when
you run "terraform init" in the future.
Terraform has been successfully initialized!
You may now begin working with Terraform. Try running "terraform plan" to see
any changes that are required for your infrastructure. All Terraform commands
should now work.
If you ever set or change modules or backend configuration for Terraform,
rerun this command to reinitialize your working directory. If you forget, other
commands will detect it and remind you to do so if necessary.
This is not for general usage, but an „admin-Jumphost“-computer/vm which needs to get flash enabled from time to time and is never used for public internet browsing…
There it might be an un-dogmatic solution to install the last Firefox 78.15 ESR Release.
Find it here: https://ftp.mozilla.org/pub/firefox/releases/78.15.0esr/win64/de/
That’s easy
That’s harder – Firefox guys (think to) know better what’s good for their users and they don’t even provide an „about:config“-switch: fail!
Add the following registry Key:
HKEY_LOCAL_MACHINE\Software\Policies\Mozilla\FirefoxAdd the following 32-Bit DWORD
DisableAppUpdatewith value set to
1and restart Firefox.
No „do you really want to leave“ windows any more, how nice is that!?
https://romanisthere.github.io